We are here to learn What cyber security is and how it is affecting our day to day life.
What is Cyber security?It is a process,design or architecture that is designed to protect network and devices from attack,damage or unauthorised access.Cyber security might not seem like an emerging technology, given that it has been around for a while, but it is evolving just as other technologies are. That’s in part because threats are constantly new. The malevolent hackers who are trying to illegally access data are not going to give up any time soon, and they will continue to find ways to get through even the toughest security measures. It’s also in part because new technology is being adapted to enhance security. As long as we have hackers, cybersecurity will remain a trending technology because it will constantly evolve to defend against those hackers.
-
- PROS:-
- Protect your personal data.
- Increase productivity
- Stops your website from crashing
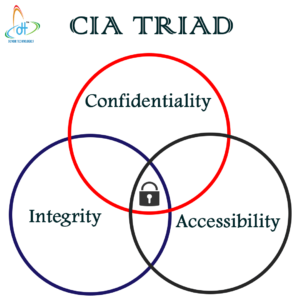
- Why Cyber security?There are three main pillars of cyber security reason behind this reason.
- CIA(CONFIDENTIALITY,INTEGRITY,AND AVAILABILITY)
- PROS:-
-
-
- Confidentiality:-It asserts that data,information and resources are protected from unauthorised access and available only for authorised access. Ex:-Bank Management System.
- Integrity:-It assert that the data should be maintained in a correct state and any unauthorised access shouldn’t be able to improperly modify it,either accidentally or maliciously. Ex:Incorrect data entered by a user in the database.
- Availability:-It ensures that this data will be available to all the authorised users,when and where they want. Ex:-Gmail,Social media(We can access our account whatever the location is).
-
- Threats to CIA:- CYBER CRIME

-
-
-
- Cyber Crime:-It is any criminal activity that involves a computer network device or network to access anybody personal data without their permission or authorisation.
- Why these cyber crimes?Cybercrimes are carried out to generate profit for cyber criminals by stealing personal data,damaging or disabling them,spreading malware etc. Ex:-System Hijacking,Dos(Denial of service),Fraud,Bank Hijacking.
Our company follows all the security measures,updates and patches firewalls,validation from both sides(client and server) and provides best,secured products to our client.
-
-


